In my last blog post, I wrote about the increased privacy of iPhone with FaceID, now I want to talk about the opportunities for developers and how they can take advantage of the contentious function for authentication.
For developers, it is possible to make user authentication easier with FaceID. For this, the application does not get facial data, only a Boolean answer, yes or no, does the face fit or not.
authenticationContext.evaluatePolicy(
.deviceOwnerAuthenticationWithBiometrics,
localizedReason: "We use FaceID to confirm you",
reply: { [unowned self] (success, error) -> Void in
if( success ) {
//FaceID successful matched
}
This code snippet shows the only way for developers to verify with FaceID, is the user, the owner. By the way, this is the same code used to check the Fingerprint.
Looking how FaceID is stored on the device, it quickly becomes clear that there is no way of getting access to it from the Internet.
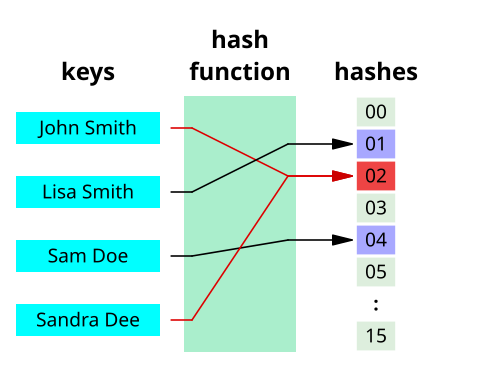
The biometric data is stored as a hash. A hash, is a combination of numbers, uppercase, and lowercase letters. “A hash function is any function that can be used to map data of arbitrary size to data of fixed size. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. One use is a data structure called a hash table, widely used in computer software for rapid data lookup.” ( https://en.wikipedia.org/wiki/Hash_function)
The hash is stored locally on the device and compared with the recognized face.
The critical opinions on the subject of data protection of FaceID are therefore unfounded, quite the opposite, in my opinion, this technology even increases the data security of users.
Users no longer need to remember their passwords, so they can use more complex passwords.
In my opinion, FaceID is a good step forward for more privacy.